Hello Crypto Prof @stream4u !
This week was marvelous after learning and appreciating how the cryptography and digital signature works on our blockchain platforms , below is my home work task for this week :
Explain the Blockchain Cryptography and mention few names which are the Blockchain Platforms

In our daily life we work and save money for future used , let cast our mind back to what happens in our traditional Banks where you save your own money but it require some processes before your money is released to you all because of security , Before your savings are released your signature is used to confirm that you are the right owner of the fund ,and bankers will advise customers to have a signature that can’t be imitated ,it should unique and easily verifiable when using it , all this is because of security this is what in blockchain we refer to as cryptography but then it works different but they are meant to achieve the same purpose.
Blockchain Cryptography: This is a combination of two words which are crypto + graphy whereas crypto means secret and the graphy means writing, so basically cryptography is as a technological method of sensing a message that is secured among others or a person where by the sender hold a unique type of code that will encrypt the message before he send, before the receiver get access to the message he/she has to decrypt it using a specific key.
When the message, data or transactions are encrypted it is not possible for anyone without the correct keys to read them.
In cryptocurrency cryptography can be seen as symmetric and Asymmetric depending on how the message decrypted, Cryptography in blockchain can be used for so many things including:
Security
Protracting the minting of new coins
Verification of Transactions.
Below are some of the blockchain platforms that uses cryptography :
Ethereum Blockchain
IBM Blockchain
Bitcoin Blockchain
EOS Blockchain
Tron Blockchain
Explain the Public Key Cryptography.
This type of cryptography uses two powerful mathematically generated keys known us the Public keys and the private keys, these pairs of keys are like brothers that cannot do away with each other, each public key has a unique private key such that when public keys are used to encrypt a data only their corresponding private keys can be used to decrypt it.
One impossible thing is that one cannot generate or fabricate a private key because they have access to the public key, it requires a computational process to generate a private key.
So during this cryptography procedure the receiver have to share their public keys with the sender so that the data can be encrypted and sign digitally so that when the message is released the owner of the private key will then decrypt it.
The public key is very complex, big and not easy to remember so they are usually stored in a digital certificate form and the other one which is the private key can be stored in one’s computer or drive.
Explain the Private Key Cryptography.
One thing that is crucial in cryptocurrency is your private key, it is believed that your private key is your money, once a wallet is created the owner of the wallet is given a public key and a private key, the private key are not meant to be shared to others, this key combined with digital signature are used to verify a user before a transaction is authenticated to them.When sending a data or a crypto token to someone the private key is requested to confirm the transaction and the receiver can also access the coin by verifying that he is the owner of the public key or address on which the sender released the token using the private keys.
Explain the Digital Signatures Cryptography and what is Singing Of Transaction/Message?
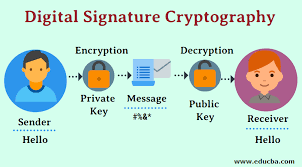
DIGITAL SIGNATURE CRYPTOGRAPHY: This is an electronic signature that is generated using powerful mathematical computations that is used to verify the originality and protect the rectitudeness of the message.
This signature help to put a virtual fingerprint of an authentic owner on data and this print is unique to the person such that no one can replicate it easily.
This has gone a long way to enhance transparency in cryptocurrency industry and it lead to trust a mong peers.
HOW DOES DIGITAL SIGNATURE CRYPTOGRAPHY WORK
This digital signature helps us to know the authenticity of a data, usually what happens is that a hash will be generated for they data and it will encrypted to the private keys of the sender, as we learnt last week the hash is very unique to the data or message been encrypted so any alteration in it will not work.
After the data is been digitally signed it is then transmitted to the recipient ,using the senders public key the receiver can generate a hash to decrypt the message after which these two hashes are compared IE that of the sender and receiver if they are similar this indicate that the transaction is not modified.
SIGNING OF TRANSACTION
During transaction like sending Steem to another address the sender usually generate a transaction that need to signed before it is sent to the recipient, some mathematical computation occur in order to generate the digital signature using the private key of the sender, the private key that sign the data or the transaction has a unique public key that the receiver require to generate a hash to confirm that the transaction is not modified.
So basically signing of transaction is the use of a private key to sign a transaction such that the transaction is encrypted and tag with a unique hash.
Explain what is Symmetric and Asymmetric cryptography?
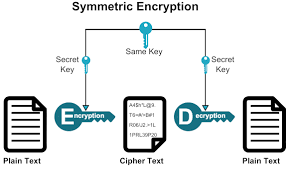
SYMMETRIC CRYPTOGRAPHY:This a type of cryptography where by a single unique key derived using a mathematical algorithm is used to encrypt a data or message and when transmitted to the recipient the same key is used to decrypt the data , in this case there is only one single key that is pass on to the recipient.
.png)
So basically this cryptography deals with just a single key usually called a secret key and it is the only key that decrypt and encrypt the data transmitted.
I have also identified that the symmetric cryptography can be in two forms which are:
- Stream Algorithm : this use the secret key to encrypt data such as digits and letters of a particular message individually , let say I want encrypt STEEM , this algorithm will encrypt it in bit like S-T-E-E-M and it won’t store the data in the system memory as well.
- Block Algorithm : This one is also a cryptography process that encrypt a number of letters or digits let say bits at a goal and the encrypted bytes are kept in a block while the encryption is going on the data is also being stored in the system memory .
SOME EXAMPLES STATED BELOW :
Some examples of symmetric encryption algorithms include:
• >AES (Advanced Encryption Standard)
• >DES (Data Encryption Standard)
• >IDEA (International Data Encryption Algorithm)
• >Blowfish (Drop-in replacement for DES or IDEA)
• >RC4 (Rivest Cipher 4)
• >RC5 (Rivest Cipher 5)
• >RC6 (Rivest Cipher 6)
ASYMMETRIC CRYPTOGRAPHY: This is a cryptography popularly used among many cryptocurrency blockchains, it requires two keys which are the public key and the private key.
From some of my explanation above I stated that each private key has a unique public key, so in this type of cryptography what happens is that the sender encrypt a data or message on the public key of the recipient such that only the recipient private key corresponding to the public key used can decrypt the message.
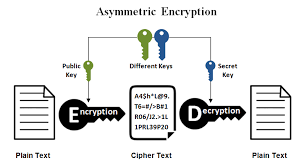
The process of encrypting and decrypting usually happens without users’ involvement it is automated once the nodes confirm the keys are authentic to the message.
Some important things we have to note about this type of cryptography is that :
- Private keys are safe since they are not transmitted or exposed to anyone
- It used digital cryptography signature to protect the data for the recipient to verify the data.
- Here it is hardly a sender will lie about transmitting a message
Finally I will share one problem with this type of cryptography it is not fast compare to the symmetric cryptography so if you want to use it for encrypting large data it will delay your work.
How Blockchain Wallets Cryptography works and explains the available types of Crypto Wallets.
First of all let get to understand the meaning of wallet in crypto , this is just like our normal bank account where our transaction an funds are recorded , with crypto wallet the private key of the owner of the wallet is stored safely in it and it can easily be accessed .
As we all know that in cryptography every private key has a corresponding public key, same apply here as well it enable wallet owners to send, receive cryptocurrencies.
Before a wallet record a transaction or let me say before money is sent to a wallet the public key of the wallet, the wallet will hash a digital signature using the public address to generate a wallet address which is usually giving out to the sender to transfer the cryptocurrency, so from this we can see that there is a kind of Asymmetric cryptography used here, the recipient can only have access to the coin by suing the corresponding private key used to generate the wallet address.
Upon all this process one thing we have to note is that until an intruder get hold of your wallet private key they cannot steal your crypto, so wallet allow owners to set an extra password or fingerprint aside the cryptography security.
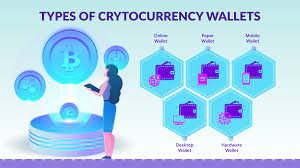
Crypto Wallets are always seen in two ways and categorized under three groups. The two known ways we see crypto wallets are those that get connected to the internet and known as hot wallet and those that stay offline known as Cold Wallets.
Considering Wallet under categories we have the following:
- Software Wallet : this are wallet generated in a form of software program like mobile Apps as it name implies , so we can say they are Hot wallet because they work being connected to the internet some few examples are :
1.) Mobile Wallet
2.) Online Wallet
3.) Desktop Wallet
- Hardware Wallet :This category of wallet can also be clearly defined from it name , they are wallet that can be seen physically and touched like computer hardware ,the wallet usually stores it keys offline but they act like peripheral device to the internet although they store keys offline but they must be connected to the internet to work.
Examples:
1.) Ledger Wallet
2.) Trezor Wallet
- Paper Wallet: As the name suggest this wallet has it detail spelled out on a printed paper the details can be copied or scanned during transactions it also has a QR-Code options. It is known to be very secured because it can be used offline as well as online ,during transaction what happen is that the sender either scan the QR-Code or copy the wallet address on the printed paper.
What is the Merkle trees and what its importance in blockchain?

Before we understand what Merkle tree is, let rewind our brains to what Crypto Prof @stream4u discussed last week about blockchain, we learnt a blockchain comprises of different block with unique Hash, Cryptography but they are all linked such that the hash of the precious can be found in the next, so let ask ourselves if the hash is been interconnected this way what about the cryptography and digital signatures that secure the block as well.
Analysing this you will come to realize that there will be a whole lot of cryptography and digital signatures in a blockchain, this is where the man called Ralph Merkle inverted the Merkle tree that can minimize the memory size these cryptography and digital signature would be taking, so now let get to know what Merkle Tree is.
MERKLE TREE: This is system that brings together all hashes in a blockchain such that they are represented by a single algorithm address called the Root hash , making validation simple because miners don’t have to validate every hash in the blockchain they only have to take up the Root Hash comprises the hashes of all blocks in the system.
.png)
Looking at the picture above you can see that the Hash root is at the top and different hashes join to form the root start from the button.
To best explain this let read the image from the bottom, every hash in the bottom two rows (HH-HA) AND (TT-TA) are called the leaves and the ones in between the Hash root and the Leaves (HGH-HAB) AND (HABCD –HEFGH) are branches, hence we have a tree which is the Merkle Tree also known as Binary Hash tree because of the additions it does to get a single root.
- It makes validation for blockchain miners easy such that they don’t have to go through all the blocks in the blockchain.
- It saves space and make Computers fast , instead of storing every hash on the computer Merkle tree will reduce the space to be used
- There is much credibility and integrity in any blockchain because when a hash is tempered with the Root Hash changes.
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, and Blockchain with proper screenshots of yours practical
KEY
In cryptography we are aware that there are two keys available which are the public keys and the private keys this keys are linked to each other such that every private key has it corresponding public key, and during the generation of a wallet address the public key is used hence to validate a transaction involving the public key it corresponding private key is required.
Practically let look at how this two function:
.png)
From the above image we can see that the private keys selected randomly have their public keys generated along and any time you click on random a new public key is generated, now let try creating our own private key and see if we will have a unique public key to it.
In this practical session I will use 554411370 as my fist private key:
.png)
When I was typing the new private key I realized the public keys was also changing till I typed fully the new private key, this tells you that they are linked to each other.
The public key for the private key 554411370 generated is:
04da83d30b6ddfadb5289d4b0f87e118c587f4e983711a451eaec1b937b45e4ce614dd9701df578085ea87d294d88d855f3503ceee5c281c6b58ba8fd6609256dd
SIGNATURE
Signature are generated to protect data such that only the private keys of the address that was signed can access the data, in the practical below I will be signing the message GHANA MY COUNTRY , using the private key 554411370 .
.png)
After clicking on the sign the signature to the message GHANA MY COUNTRY was generated as below :
.png)
Now let verify the signature, so I will have to enter the public key of the private key 554411370 as shown below:
Let look at before verification
.png)
After verification
.png)
From the image above we can clearly see that the interface changed to green indicating that the signature and the message is verified, let change the public key and see if it will be verified:
.png)
After changing the public key in the above image let look at what happens next, the entire interface turned red.
TRANSACTION
Here we will be looking at how transaction works with digital signature , from the image below we have a transaction whereby the private key 554411370 has an address generated in relation to the public key of the private key stated , transferring $100 dollars to another wallet address shown in the image below .
.png)
From the previous practical explanation above you all realize that the private key is require to sign the transaction so I have entered it and after clicking on sign the signature was generated and now time to verify it :
.png)
Before the verification can be done you have to type in the signature generated for the transaction and click on verify once the interface turn green it show the transaction is verify and the private key is the authenticated
BLOCKCHAIN
Here we are going to practice how secure a blocks are stored in a block chain using cryptography and we will also remind ourselves of what we learnt last week about how the blocks are interconnected as well.
Let consider the block 2
.png)
The digital signature sign was for $10 and I will want to alter it let say I am scam and I want to do double spending so I want to change the transaction amount to $20.
After Changing the amount let see what happened:
.png)
Everything changed red even all other blocks in the blockchain also turn red because the change affected the hash hence it will affect the previous hash stored in each next block.
To make this transaction valid unless we mind this using a computer if you want to use human power it will take you years to be able to generate a correct hash , hence let click on mine and see what happens
.png)
The hash was mined successfully but the signature still seems to be red indicating that the signature does not much the private key and the amount entered hence we can clearly see how difficult it is to change what has been signed digitally.
NB:ALL PICTURES WHERE SCREEN SHOTS MADE FROM SOURCE
In Conclusion I will like to say that this lesson has broaden my mind on how secure blockchain transactions are , because looking at what cryptography does you can realise that once your private keys are kept safe everything you do on blockchain is safe.
I got to know the importance of wallet address in relation to public keys and how data are been encrypted using digital signature in cryptography.
I will want to use this opportunity to thank the entire Steemit team for a wonderful work this week again and say kudos to the crypto prof @stream4u for bringing to us this wonderful lesson this week.